
On Saturday, multimedia producer and Twitter user Daniel Dennis Jones — @blanket, at the time — received a notification that his Twitter password had been reset. This alone would have been cause for concern; at the very least, it would mean that someone had tried and failed to access his account. He quickly found out that the problem was much worse:
Tried to login and failed. Was still logged in on my phone though, and was panicked to see my tweet/follow counts at 0.
 Tried to login and failed. Was still logged in on my phone though, and was panicked to see my tweet/follow counts at 0.-- Daniel Dennis Jones
Tried to login and failed. Was still logged in on my phone though, and was panicked to see my tweet/follow counts at 0.-- Daniel Dennis Jones
(You can find a first-hand Storify of Jones's experience here. It's long but worth reading.)
He was eventually able to log back into the account, but found that his username had been changed to @FuckMyAssHoleLO (I can only assume the last "L" got truncated), and that @blanket was now operated by someone else. His account, in other words, had clearly been hacked.
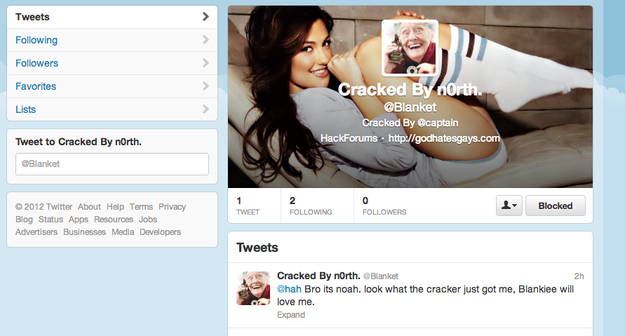
In addition, his username had been put up for sale. All apparently due to an incredibly obvious Twitter security flaw — one that the company has so far treated as a standard support issue.
Jones found his username listed among other single-word names on a site called ForumKorner, a community where users can buy and sell usernames for online games, a common practice that's not always sanctioned by game companies. It's also, apparently, at least an occasional marketplace for illegally obtained Twitter accounts:
By chasing tweets I find @blanket & others are being pimped at a site called forumkorner http://t.co/kWRING5N
 By chasing tweets I find @blanket & others are being pimped at a site called forumkorner http://t.co/kWRING5N-- Daniel Dennis Jones
By chasing tweets I find @blanket & others are being pimped at a site called forumkorner http://t.co/kWRING5N-- Daniel Dennis Jones
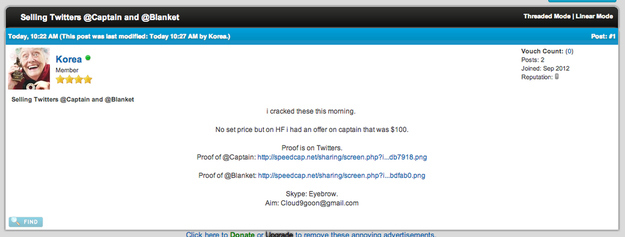
Using forum usernames a little bit of simple Google research, Jones was able to find multiple stories like his own: people with desirable usernames who were blindsided by account theft, and who found their usernames listed as available by a small ring of teen hackers. The hackers, Jones discovered, not only sold some of these usernames (for surprisingly low sums, by the way — rarely more than $100), but gave others to friends. A quick scan of their timelines reveals a suspicious number of single-word, hard to get — or as the hackers call them, "OG"— user names. These people, it seems, have discovered how to steal highly coveted usernames.
This would be indicative either of some kind of basic Twitter exploit or some clever social engineering, much like what Wired's Mat Honan rivetingly recounted a couple months ago. When Jones confronted a hacker he found on Twitter, who he told BuzzFeed was likely an "acquaintance" of his own hacker, he was told it was the former:
4:54:30 Jones: what makes a name easy to jack? a vulnerable password?
4:55:15 Moon: yes
4:55:47 Jones: do you rely on lists of other passwords, like the linkedin hack? or do you randomize passwords? how does the cracker work?
4:56:17 Moon: i have several custom pw lists that i've made my self
The hacker described an exceedingly basic technique: he used a program that repeatedly attempts to log in with common passwords. Most sites, including Twitter, flag or disable user accounts, or throw up a CAPTCHA, after a certain number of failed login attempts. But whereas many services, including Gmail, limit login attempts on a per-account basis, Twitter apparently only prevents large numbers of login attempts from the same IP address.
In other words, hackers — or crackers, as they would call themselves — can try to log in as many times as they want, so long as the login attempts appear to be coming from different computers.
5:16:07 Jones: No, twitter - since twitter is easier than youtube - what would twitter have to do to make it as hard to crack as youtube
5:16:38 Moon: they would have to redo they're captcha system, youtube uses a more complex one,
5:16:49 Moon: that filters by account, unlike twitter which filters by ip
Jones says that in a way he's fortunate, telling BuzzFeed FWD, "I don't take Twitter terribly seriously in my life, so I'm glad it's been isolated to that."
"There are people out there whose twitter names hold a lot more concrete value to them," he says.
Beyond the initial theft, he says, the hackers exhibited little malice, leaving his account intact and refraining from scorched earth hacker tactics. "It could have been a lot worse," he said, "I feel lucky that what happened to Mat [Honan] didn't happen to me." Mostly, he says, the hackers were just trying to make a quick buck, or impress their friends (and girls) by scoring them short new handles.
Jones admits his password wasn't particularly strong, which helped make this hack possible. But if his hacker is telling the truth, this is a massive security hole in Twitter. It's one that the site could easily remedy, of course, but also one that shouldn't exist in the first place. Jones says the support system at Twitter seems "intentionally opaque," and that his interactions with the companies — through official channels and through friends of friends at the company — haven't been encouraging. Jones will continue to document his experience on Twitter and Storify, including his interactions with the company. (I've reached out to Twitter for comment, but before PST work hours. I will update if I hear back.)
"I've been able to clean up some things and make the general public aware," Jones says. He hopes his experience will help others out: "It's like when you read a scary story and lock your door — people should be changing their passwords."
Update: Reader Sean Savage writes:
Thanks for throwing light on the issue – I've got username @savage on Twitter, and my account is constantly under attack. At least 3-4 times per week, sometimes a couple times a day, I receive password-reset messages from Twitter. (That is: The standard message you get if you click "Forgot your password?" on a site, and the site sends you an e-mail with a unique URL link that will open a Web page letting you change your password.)
I've tried to contact Twitter over and over and over again about this over the past year or so, and never received a satisfying response. The only responses I've gotten just repeat the basic sort of passwords-101 info that you see on any site's FAQ pages. (Of *course* my password is strong, not a dictionary word or my name etc.) When I finally did get a response from an (apparent) actual human, they told me to just ignore all the incoming "here's how to reset your password, as you requested" e-mails.
The incessant reset requests suggest to Savage that his hackers are using a different technique — the method described by "Moon" doesn't seem like it would trigger so many. Savage also notes a recent addition to the emails, in the form of a new security feature: "If you're getting a lot of password reset emails you didn't request, you can change your account settings to require personal information to start a password reset."
Update 2, 2:27 PM EST: Dan Jones says his username has been restored by Twitter.
