UPDATE
On March 31, Pornhub announced that it is officially switching to HTTPS and is turning on the encryption protocol by default. YouPorn, which is owned by the same parent company as Pornhub, is moving its site to HTTPS on Tuesday, April 4.
Most adult websites, but especially free "tube" sites, don't use HTTPS, a secure web protocol that gives visitors an extra layer of security.
With plain HTTP, anyone – like hackers, the government, or snooping neighbors – sitting between your browser and the webserver can see what’s moving back and forth.
“Live cam” sites, like Chaturbate, LiveJasmin, and Bongacams, are more likely to have HTTPS protections than other types of pages – but free “tube” sites (the ones that don’t require payment to watch adult content) have been slow to adopt the secure protocol. Of the top 11 adult websites in the world, according the latest Google Transparency Report, only three offer HTTPS by default: Chaturbate, xHamster, and, most recently, RedTube.
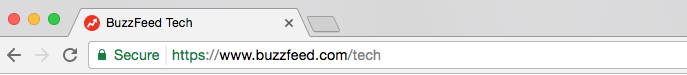
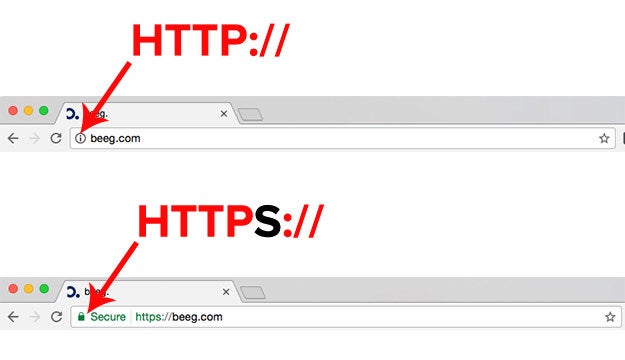
That’s alarming. HTTPS is important because it encrypts the data on a webpage, making it difficult for an interested third party to see what you’re looking at. Larger sites like Amazon, Google, and Facebook use it to give their users an extra layer of security. You can tell whether the site you’re on has HTTPS by looking for a padlock (Safari) or “Secure” (Chrome) next to the URL in your browser.
“A lot of websites use logins, and a lot of adult sites, even the premium ones, are sending usernames and passwords unencrypted out on the wire,” explained Richard Barnes, Firefox’s security lead. “What’s worse about the passwords is that people re-use those passwords for email, Facebook, and other sites.”
The HTTPS secure web protocol also has another benefit, in addition to encryption. Using a virtual “certificate” required to enable HTTPS, the browser can verify that you’re actually looking at the webpage you intended to, and not some version of the site modified by another party (usually a hacker). This type of hack is known as a “Man-in-the-Middle” attack and it was most famously used by the Chinese government, in what was called the Great Cannon.
Basically, HTTPS protects what you’re looking at from people interested in surveilling you. It also protects the information you submit to the website (like credit card numbers, usernames, etc.). That sounds like a REALLY good precaution for any website to take.
Think twice about visiting these unsecure sites.
Pornhub, which was visited 23 billion times last year, doesn’t offer HTTPS. Neither do tube sites Youporn and Xnxx, or image hosting sites Imagebam and Pzy.be, often used to upload adult photos and videos — and all of which are listed on Google’s top 100 (non-Google) sites by web traffic. Other popular sites that don’t offer HTTPS are Porn555 and Txxx.
Beeg and Xvideos have HTTPS – but be careful – it’s not turned on by default. If someone sends you an unsecure, plain HTTP link to either of those domains, the site will load without HTTPS protection. You can use a browser extension called HTTPS Everywhere (free, Firefox, Chrome, Android, and Opera) to force those pages to request HTTPS.
So why don’t all sites have HTTPS?
It costs money for big porn sites to set up HTTPS, and they have to figure out logistics with advertisers. Many web analytics and advertising resources load over plain HTTP, rendering HTTPS sites vulnerable. Not only must the site itself use HTTPS, but so must all of its third-party elements.
Alex Taylor, the vice president of marketing at RedTube, a free porn site that receives 20 million daily visitors, explains why implementing HTTPS isn’t so easy for online content providers: “The greatest challenge in becoming HTTPS was getting all of the advertisers and advertising networks on board for the switch. Costs of certificates, additional streaming costs, and making sure all of our providers are ready for the switch are other obstacles we faced.”
RedTube switched to HTTPS, Taylor said, because it "wanted to promote safe sex, whether it be in ‘real life’ or online,” as well as to ensure that visitors can “browse and view content with complete confidence.”
If you’re going to risk visiting an HTTP porn site, never visit it over public Wi-Fi.
If you’re on a shared network at Starbucks, a hotel, college campus, or other public venue, someone can easily snoop on your plain HTTP pornography session – and see what videos you're watching, plus any data you send to that site, including usernames, passwords, personal info, and credit card information.
“On public Wi-Fi, it doesn’t require a lot of technical sophistication,” warned Firefox’s Barnes. “Someone wrote a Firefox extension called Firesheep and it’s a pretty easy-to-use tool that shows you everyone’s logins.”

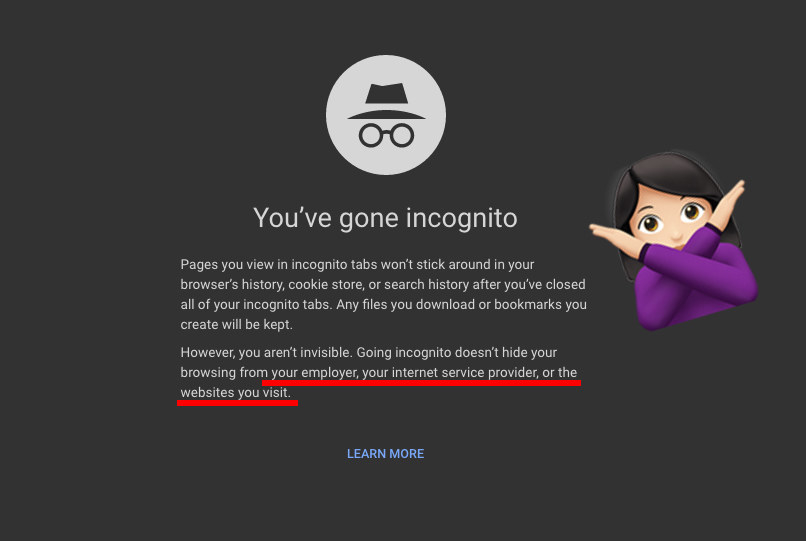
BTW, even if you’re on an HTTPS site, “incognito mode” and “private browsing” aren’t as private as you think.
Chrome does offer this warning in incognito tabs: “Going incognito doesn’t hide your browsing from your employer, your internet service provider, or the websites you visit.”
While incognito in Chrome and private browsing in Safari do prevent those tabs from being recorded to your browser’s history, cookie store, or search history, it doesn’t make you untraceable. It means that your browser will stop tracking you, but the domain will still be logged in your corporate network if, for example, you’re at work or using a company machine.
Your internet service provider (ISP) also has access to a list of all the websites you visited, whether you’re in incognito or not, and government agencies will still be able to surveil you. Joseph Lorenzo Hall, chief technologist at the Center for Democracy and Technology, calls Chrome’s incognito mode the “most ill-named thing.”
So, basically, don’t watch porn at work. Incognito mode won’t save you.
Be vigilant about where you click: Malvertising is particularly bad on adult websites.
Malvertisements are “malicious advertisements” that may contain spyware, and if you click a bad link, they give hackers a window into everything you do on a device.
“The adult industry has had problems with malvertising, especially where the ad content was changed after the ad was submitted,” said Hall.
If you get a pop-up ad while you’re on a porn site, a) figure out if it’s fake by reading the warning and looking for typos and urgent language (a lot of exclamation points are a good indication), and b) take a second to figure out how to safely close the pop-up without clicking on the wrong thing. Deceptive “no,” “cancel,” “close,” or red “X” buttons may be designed into the ad itself.
If it’s a really tricky pop-up, quit your browser entirely and prevent your old pages from loading, instead of trying to attempt to close the pop-up window:
* On Mac, if you’re using Chrome, see if you can move the window > go to chrome://settings/ > under On Startup, select “Open the New Tab page” > command+option+esc to open Force Quit and select Chrome.
* In Safari, use command+option+esc to force quit Safari and hold the shift key while re-launching Safari to prevent windows from the last browsing session from reopening.
* In Windows, right click on the pop-up in your Taskbar and click Close.
Ransomware, which can be delivered through malvertising, is a particularly devastating type of attack that saw a huge increase in 2016. Ransomware programs allow hackers to hold their victim’s electronic data hostage and threaten to delete everything until the victim pays a fee. This attack is typically distributed via malicious email attachments, but bad links from pop-ups, social media posts, and messaging apps can also infect your system. There are two types of ransomware: “locker,” which prevents users from accessing their device, and “crypto,” which encrypts all of the device’s data, rendering it unreadable until the ransom is paid.
I know some of you are thinking “DUH” x a million. Obviously windows that read, “Your computer has a virus! Download this” or “Congratulations!!! You are a winner!” should. not. be. clicked. But sometimes you don’t even have to click an ad to fall prey to malvertising.
To protect yourself, install an ad-blocker plug-in, never allow pop-ups, and disable Flash and Java.
Malware ads like these are why Hall at the CDT is urging all web users to use privacy extensions like Ghostery, Adblock, and Noscript, which remove some programmable elements like tracking scripts on pages. These privacy extensions also have the added benefit of speeding up load times and cleaning up webpages.
“With Ghostery, the ads won’t load, or they’ll load with just a picture. Using one of these extensions is a much better way to protect yourself right now,” Hall said.
Turning off pop-ups by default may also help curb the risk of an attack. In Chrome, go to chrome://settings > Show advanced settings > Content settings > under Pop-ups, select “Do not allow any site to show pop-ups.” You can also block pop-ups on specific sites and click on where it says “Secure” (HTTPS site) or an “i” information button (HTTP site) to the left of the URL and click the dropdown menu next to Pop-ups, then select “Always block on this site.”
You can turn off Javascript from the browser’s settings, too. In Chrome, go to chrome://settings > Show advanced settings > Content settings > JavaScript > Do not allow any site to run JavaScript. In Safari, go to Preferences > Security > uncheck Enable JavaScript. You can also click Plug-in Settings to configure Adobe Flash Player settings.
Stay safe out there!
Don’t be shy: Have “The Talk” about security risks on adult websites with the first-time cybercitizen in your life — or share with your friends who wouldn’t consider themselves tech savvy.
