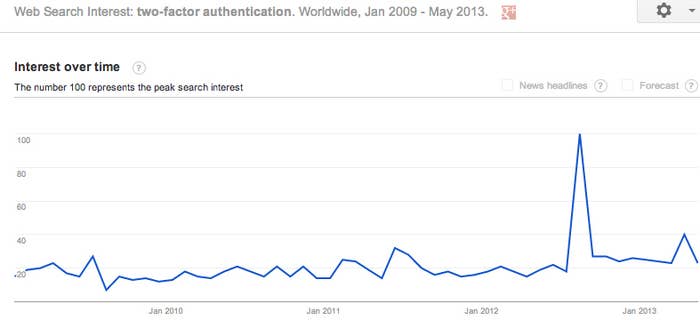
As high profile hacks continue to make news, "two-factor authentication" is becoming a household term. This year alone, Apple, Microsoft, and Evernote have rolled it out to users, and two weeks ago Wired reported that Twitter is developing a two-factor option of its own. Google and Facebook have had it since early 2011.
It's usually described in the media as a sort of silver bullet: Damaging Twitter hacks, the thinking goes, will cease as soon as two-factor authentication becomes available.
Now, security experts are questioning its limits. As cyber attacks grow more sophisticated, hackers are zeroing in on mobile devices with the express intention of circumventing two-factor auth — an integral part of the two-factor process, which requires users to interact with their phones, either through text message or app, to log in. "In underground communities we're seeing a lot of chatter focusing around mobile, specifically with phones," Daniel Cohen, Head of Online Threats Managed Services at RSA tells BuzzFeed. Cohen notes that Trend Micro has seen 35,000% percent growth in Android malware between 2011 and 2012, from 1000 samples to 350,000.
"We're seeing apps that will steal your contacts off your phonebook as well as applications that are programmed to steal SMS messages. These programs hide the messages from the users, so you'll never even know you received the SMS," Cohen said.
This kind of mobile malware — which can find its way onto your phone through a corrupted site or a compromised app — successfully grabbed private SMS data in Europe as part of a dramatic online heist. A December 2012 study by Versafe and Checkpoint Software Technologies details a Trojan virus called the "Eurograbber," which stole over 36 million Euros from bank customers masking itself as a bank's mobile encryption software. A passage from the report chillingly explains how the virus works:
The bank's SMS containing the Transaction Authorization Number (TAN) is the key element of the bank's two factor-authorization. The Eurograbber Trojan on the customer's mobile device intercepts the SMS and uses the TAN to complete its own transaction to silently transfer money out of the bank customer's account. The Eurograbber attack occurs entirely in the background. Once the "security upgrade" is completed, the bank customer is monitored and controlled by Eurograbber attackers and the customer's online banking sessions give no evidence of the illicit activity.
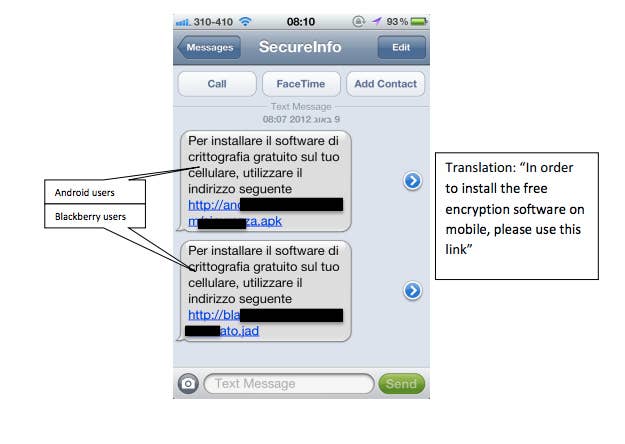
Though the two-factor breaches have, so far, been mostly relegated to the banking industry, they pose a real threat to social and personal accounts, especially as more platforms adopt two-factor security solutions and phishing scams become more personalized. Spear-phishing isn't just for organizations — scammers use it to target individuals, too.
"It's not that the tech or that the method is corrupted, it's that we as humans "fail" with regard to being vigilant and aware of the attacks," Cohen added. "That said, social engineering today is done with such high quality that it can deceive even a well trained eye."
For security experts like Cohen, these hacks are part of a never-ending cat and mouse game, where hackers are often a step ahead. Two-factor authentication is important, but in no way a panacea for online security — for hackers, it's a hurdle, not a roadblock.
As companies like RSA continue to develop more advanced methods of protection — currently, RSA is trying to build a profile of the "legitimate user" to make it easier to see abnormal behavior across the web and identify hacks — threat managers like Cohen suggest not only dual authentication, but extreme vigilance.
"The web has definitelly become more dangerous in recent years and malware much more malicious in its nature," Cohen cautions. "The security industry understands that this is a fact of life now. We have to accept that our computers can be breached and then work to find the solutions to help protect us."
